A Compliance Roadmap for Secure Product Development: Insights from DataHouse
In today’s digital landscape, compliance and security are essential for enterprise software solutions. Whether you’re developing an ERP system like VizERP or any other product, following industry standards builds trust, protects sensitive data, and ensures operational success.
With insights from Scott Fujieda, Chief Security Architect at DataHouse, this guide provides a structured compliance roadmap for businesses developing secure products.
Compliance Roadmap: A Phased Strategy
To achieve compliance, organizations should follow a phased approach, aligning security efforts with product development stages.
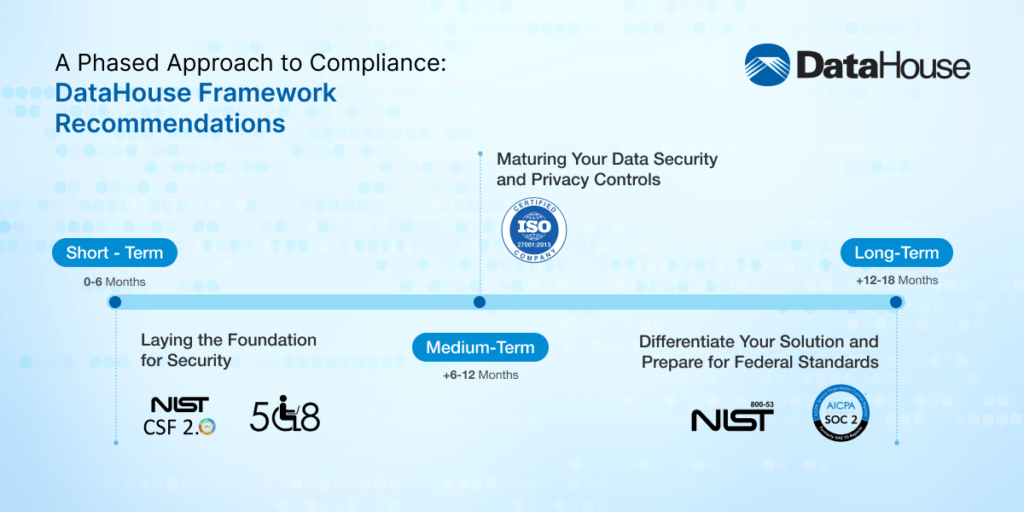
Short-Term (0-6 Months): Laying the Foundation for Security
NIST Cybersecurity Framework (CSF): A publicly available framework that provides a solid foundation of controls to build upon.
ADA (508) Compliance: Ensure accessibility for all users, particularly if your application is intended for the general public.Looking to develop a secure and compliant enterprise solution? Contact DataHouse today to explore how we can support your security and compliance needs.
Medium-Term (+6-12 Months): Maturing Your Data Security and Privacy Control
ISO 27001: Establish a robust information security management system (ISMS) to protect sensitive data and mitigate risks. As your governance and risk management policies and procedures mature, consider seeking certification from a 3rd party auditor.
Long-Term (+12-18 Months): Differentiate Your Solution and Prepare for Federal Standard
SOC 2 Compliance: Implement more granular procedures and controls to secure customer data throughout your product delivery workstreams, further aligning with strict enterprise and regulatory expectations.
FedRAMP Moderate (NIST 800-53 r5 Moderate): If your target clients include larger Government Agencies, you should start planning for how your organization can meet these controls as required for Federal contracts. Most organizations will not be able to get to this level without support from a partner, but advance planning will help you identify what you’ll need and what you can contribute to that partnership.
Key Considerations for Compliance
Before developing a software product, evaluate:
✔ Who is your target client? (Public vs. private sector, industry-specific regulations)
✔ What data will your system handle?
- Personally Identifiable Information (PII)
- Protected Health Information (PHI) (medical data)
- Federal Tax Information (FTI) (government records)
- Data from minors (<13 years old)
✔ Where are your users located? (Regulatory requirements vary by region and country)
Understanding these factors early ensures a structured security approach and regulatory alignment.
Balancing Security & User Experience
Effective compliance doesn’t mean sacrificing usability. Consider these strategies:
🔹 Phased implementation: Start with clients that have minimal compliance requirements for faster deployment, then expand security layers.
🔹 Customizable security frameworks: Adapt security levels based on client and industry needs while maintaining seamless usability.
Partnering for Long-Term Compliance Success
Compliance is more than meeting regulations—it’s about protecting users, enhancing security, and ensuring business success. At DataHouse, we help businesses navigate complex security frameworks, streamline compliance integration, and develop secure enterprise solutions.





